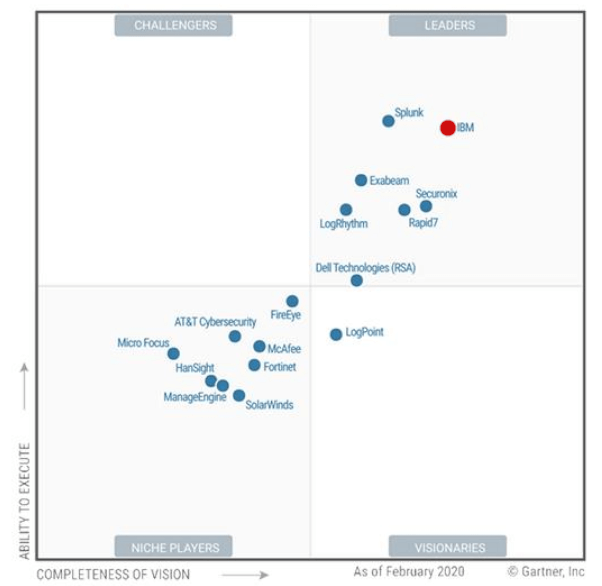
Eastern Light Technologies an IBM Gold Business Partner in KSA, offers one of the most progressive and integrated portfolios of enterprise security products and services, IBM Security. We provide security intelligence to support organizations in protecting their people, infrastructures, data and applications, ready to bring enterprise IBM solutions for identity and access management, database security, application development, risk management, endpoint management, network security, and more.
Our experienced team is ready to manage risk and implement integrated security for mobile, cloud, social media, and other enterprise business architectures, using IBM QRadar SIEM, detect and mitigate risks with IBM I2 Analyze and IBM i2 Analyst’s Notebook.